Managed ATTACK
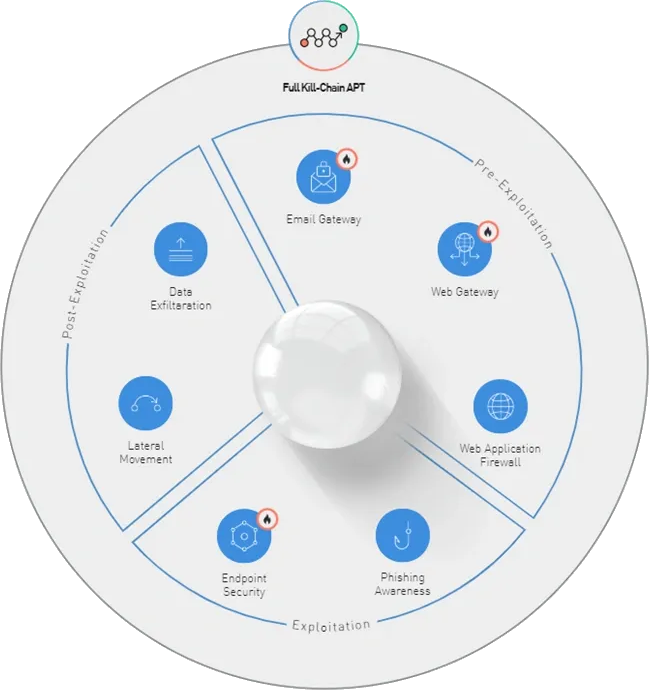
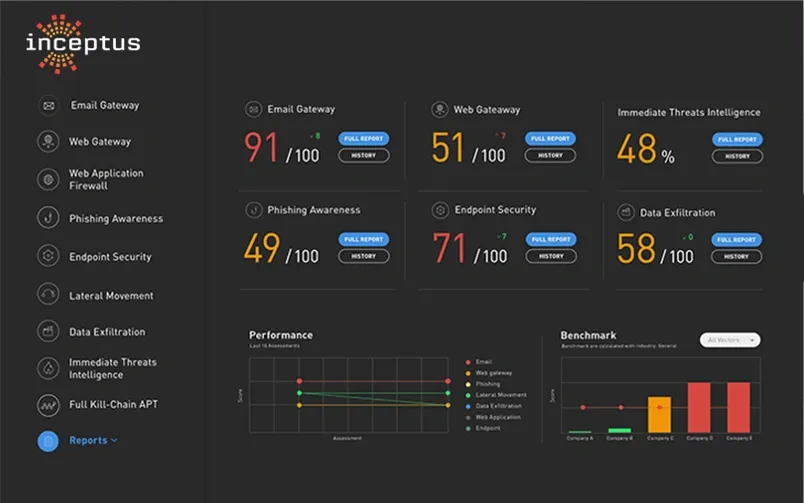
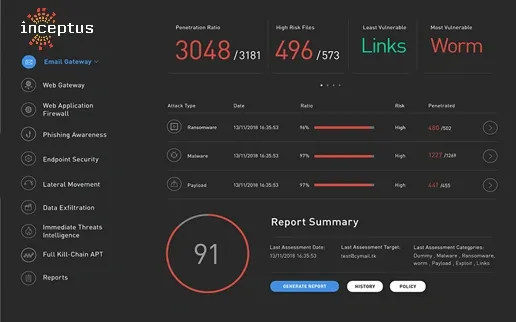
Inceptus’ Managed ATTACK performs on-demand internal and external network penetration tests, whenever you want, however you want. Managed ATTACK looks for sensitive data, performs exploits, conducts man-in-the-middle attacks, crack password hashes, escalates privileges on the network, and even impersonates users to find sensitive data. It goes beyond identifying vulnerabilities by actually exploiting them to demonstrate what happens if an attacker got access to the network.
Breach and attack simulations have made it faster, simpler and less expensive to get enterprise-grade visibility into the effectiveness of current security controls and improves an organization’s security posture.